In a recent revelation, cybersecurity researchers have uncovered a critical vulnerability that puts over a million domains at risk of hijacking. This vulnerability, known as the Sitting Ducks attack, exploits weaknesses in the Domain Name System (DNS), allowing cybercriminals to take control of domains without needing access to the legitimate owner’s account.
What is the Sitting Ducks Attack?
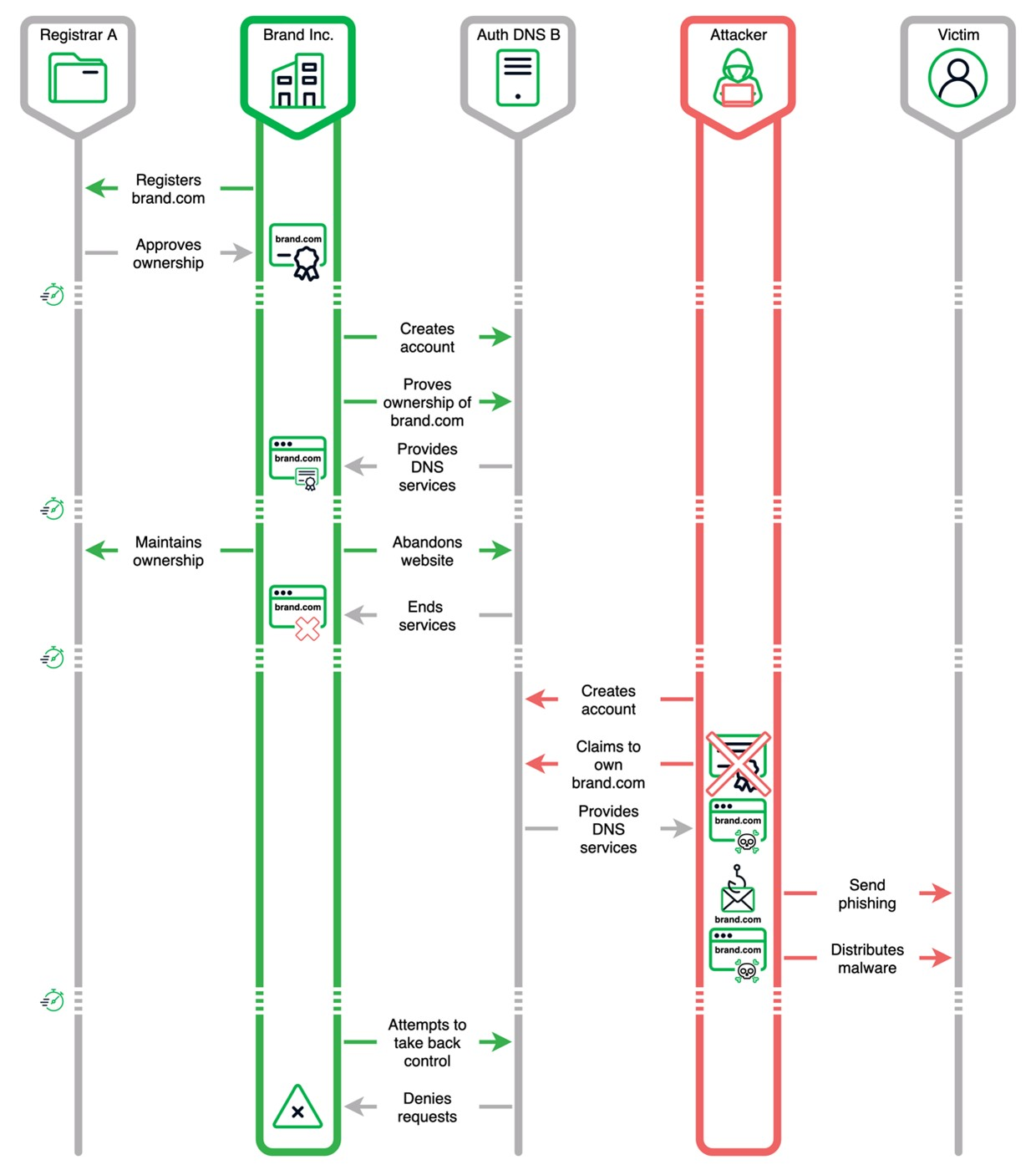
The Sitting Ducks attack is a sophisticated method that targets domains through incorrect configurations between the domain registrant and the authoritative DNS provider. If the authoritative DNS provider cannot answer authoritatively for a domain it is supposed to serve (a condition known as lame delegation), attackers can seize control of the domain. This method is particularly insidious because it does not require access to the domain owner’s account at the DNS provider or registrar, making it simpler and harder to detect compared to other domain hijacking techniques.
How Does the Sitting Ducks Attack Work?
In a Sitting Ducks attack, hackers exploit the vulnerabilities in the DNS configuration. When a domain’s authoritative DNS service expires or is improperly configured, attackers can register an account with the DNS provider, claim the domain, and use it for malicious activities. These activities can include distributing malware, sending spam, and impersonating the brand associated with the domain.
Real-World Impact of Sitting Ducks Attack
The Sitting Ducks attack has been actively exploited by more than a dozen cybercriminal groups, many of which are linked to Russia. These groups have used hijacked domains to power traffic distribution systems (TDS) like 404 TDS and VexTrio Viper, propagate bomb threats, and conduct sextortion scams. The attack’s stealthy nature and the trust associated with legitimate domains make it a potent tool for cybercriminals
Protecting Your Domain
To safeguard against the Sitting Ducks attack, organizations should regularly audit their domains to ensure they are not vulnerable to lame delegation. It is crucial to use DNS providers with robust safeguards against such attacks. Regularly checking DNS configurations and choosing reliable DNS providers can help protect your brand and prevent your domain from being hijacked.
In conclusion, the Sitting Ducks attack highlights the importance of vigilant DNS management and the need for robust cybersecurity measures. As a CERT-IN empanelled cyber security organization, Prime Infoserv is committed to safeguarding your digital assets. Our services include incident response, GRC, and managed security. Reach out to us at info@primeinfoserv.com or +913340085677. Follow us on Facebook and Instagram for updates and tips. Your security matters to us!
Stay vigilant and take necessary precautions to safeguard against potential cyberattacks.





