Introduction: A New Year, A New Cybersecurity Reality
Happy New Year. As 2026 begins, cybersecurity remains a critical focus for organizations navigating an increasingly digital environment. The New Year brings renewed ambition, reflection, and strategic recalibration. For leadership teams across industries, cybersecurity has become central to these conversations—not as a technical checkpoint, but as a business resilience imperative.
The lessons of the past year are still fresh. While digital transformation accelerated growth and efficiency, it also expanded the attack surface. Cyber incidents in 2025 demonstrated that disruption is no longer hypothetical—it is operational, financial, and reputational.
As the New Year begins, the focus shifts from simply asking “How secure are we?” to a more pressing question:
“How well can we withstand, respond to, and recover from cyber disruption?”
That question defines cybersecurity after 2025.
Introduction: Why ‘After 2025’ the Conversation Around Cybersecurity Changes; Cybersecurity attacks 2025
For many organizations, 2025 marked a turning point in how cybersecurity is understood and discussed.
The year was defined by high-impact ransomware incidents, identity-driven breaches, AI-enabled fraud, and growing regulatory scrutiny. But more importantly, 2025 exposed a gap between security investment and operational resilience.
According to industry data, the average global cost of a data breach in 2025 was approximately USD 4.44 million, underscoring both the financial and operational impact of modern attacks. Moreover, human error and behavior were involved in around two-thirds of breaches, particularly through phishing and compromised credentials, showing that even advanced defenses are often bypassed at the human layer.
Real-world breaches also drove the point home:
- A major ransomware-linked intrusion at University of Phoenix exposed the personal data of about 3.5 million people before the university publicly disclosed the incident.
- U.S. insurers including Aflac disclosed data theft impacting more than 22 million people, showing large organizations are not immune to credential abuse and lateral attacks.
- South Korean e-commerce giant Coupang faced a breach affecting over 33 million customers, emphasizing how operational and customer data can be compromised even with significant security investments.
As leaders enter 2026, the conversation is no longer centered on how many controls exist, but on a more strategic question:
“What needs to change in our cybersecurity approach so that we can withstand disruption—not just attempt to prevent it?“
Cybersecurity after 2025 demands a shift in mindset, from isolated defenses to resilience-driven strategy that integrates technology, people, process, and leadership accountability.

Looking Back: What 2025 Revealed About Cyber Risk; Lessons from 2025 Cyber Incidents
1. Strong Defenses Did Not Always Mean Strong Outcomes
One of the clearest lessons from 2025 was those organizations with mature security controls still experienced serious incidents.
Post-incident analysis consistently showed that the root causes were rarely missing tools. Instead, impact was amplified by:
- Late detection of intrusions
- Unclear incident ownership
- Delayed decision-making
- Limited recovery readiness
The lesson was sobering: security maturity did not always translate into business continuity.
This realization is driving organizations in 2026 to prioritize detection, response, and recovery capabilities as much as preventive controls.
2. Identity Emerged as the New Strategic Risk
In 2025, attackers increasingly avoided traditional network attacks and focused on identity compromise.
Stolen or compromised credentials were one of the most common initial access vectors, used in approximately 22 % of attacks, with phishing another leading cause.
Phishing, MFA fatigue, credential reuse, and privilege abuse enabled attackers to move quietly and laterally. Once identity controls failed, perimeter defenses became largely irrelevant.
Many organizations discovered that identity systems had expanded rapidly, without equivalent governance around:
- Privileged access
- Role design
- Access lifecycle management
- Periodic access reviews
Cybersecurity after 2025 places identity and access management at the center of resilience strategy.
3. Human Behavior Became the Deciding Factor
Despite advancements in automation and AI, human actions remained the most exploited element of cyber incidents in 2025.
Common scenarios included:
- Trusting well-crafted phishing messages
- Approving authentication prompts under pressure
- Misconfiguring cloud environments
- Sharing access to meet operational deadlines
Human error and behaviour were associated with roughly two-thirds of all breaches, reinforcing that technology alone cannot stop all attacks
The takeaway was clear: cyber risk is as much behavioral and organizational as it is technical.
A resilient 2026 strategy must treat human risk as a measurable and manageable component of cybersecurity.
4. Third-Party and Supply-Chain Risk Multiplied Impact
Several high-impact incidents in 2025 originated not within organizations, but through vendors, software updates, or managed access paths.
Many organizations realized too late that:
- Vendor risk assessments were periodic
- Vendor access was continuous
- Visibility into third-party security posture was limited
Cybersecurity after 2025 requires continuous third-party risk management, not one-time due diligence.
5. Cyber Incidents Became Enterprise-Level Events
By the end of 2025, cyber incidents were no longer confined to IT teams.
They increasingly resulted in:
- Business process disruptions
- Regulatory engagement
- Board-level oversight
- Reputational consequences
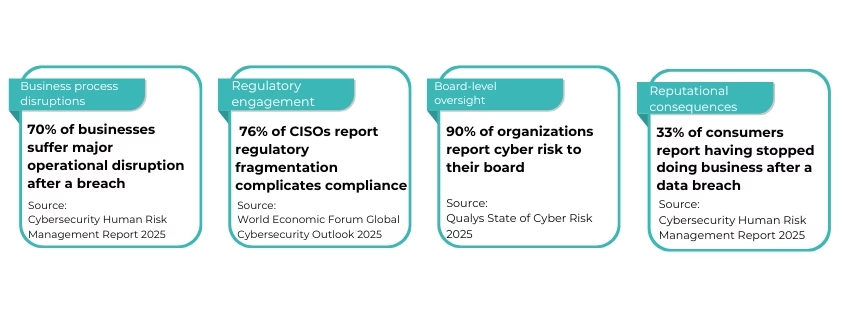
Cybersecurity became inseparable from enterprise risk management and governance, fundamentally changing leadership expectations.
Rethinking Cybersecurity Strategy for 2026
The lessons of 2025 point toward a necessary evolution in strategy.
Cybersecurity in 2026 must move beyond prevention-centric thinking and focus on resilience—the ability to anticipate, absorb, respond to, and recover from cyber incidents.
This does not mean lowering security standards. It means broadening the objective.
What a Resilient Cyber Strategy Looks Like in 2026
1. Assume Breach, Plan for Continuity
Organizations rethinking strategy in 2026 increasingly operate under a clear assumption:
- Breaches will occur
- Credentials may be compromised
- Vendors may be exploited
This mindset drives investment in security operations, threat detection, logging, and rapid containment, ensuring incidents are identified early and impact is limited.
Designing for recovery reduces disruption when prevention fails.
2. Elevate Identity Governance to a Strategic Level
A resilient 2026 strategy places identity at the core.
Key focus areas include:
- Strong identity and access management foundations
- Privileged access governance
- Least-privilege and just-in-time access
- Regular access reviews
Organizations that mature identity governance and privileged access management significantly reduce attack surface and lateral movement.
3. Treat Human Risk as a Strategic Control
Rather than relying on annual awareness programs, leading organizations are:
- Running continuous awareness initiatives
- Conducting phishing simulations
- Tracking behavior-based risk indicators
- Designing processes that reduce error-prone actions
Cybersecurity after 2025 recognizes that people are not the weakest link—they are the most targeted link.
4. Operationalize Incident Response and Crisis Readiness
In 2026, resilience depends heavily on how well incident response works under pressure.
Effective strategies include:
- Practiced incident response playbooks
- Clearly defined decision authority
- Coordination across IT, legal, communications, and leadership
- Regular tabletop and simulation exercises
Incident response maturity often determines the scale of impact and speed of recovery.
5. Integrate Third-Party Risk into Core Strategy
Third-party access in a resilient 2026 strategy is:
- Explicit and well-defined
- Time-bound
- Continuously monitored
Third-party risk management is no longer peripheral—it is integral to cyber resilience.
6. Align Cybersecurity with Business and Compliance Objectives
Cybersecurity strategies are increasingly aligned with:
- ISO 27001 and ISO 27701 programs
- SOC 2 readiness
- Data protection and privacy regulations
This alignment ensures that cybersecurity strengthens business continuity, regulatory confidence, and stakeholder trust.
Why Cybersecurity Resilience Matters in India in 2026
For India, the need to rethink cybersecurity strategy is amplified by:
- Rapid digital adoption
- Expanding digital public infrastructure
- Growth in fintech and digital payments
- Heightened regulatory focus on data protection
Reports indicate that India experienced over 265 million cyberattacks in 2025, reflecting both the scale and sophistication of attacks targeting individuals and organizations alike.
Cyber resilience across government, BFSI, healthcare, and enterprise sectors will play a critical role in sustaining trust in India’s digital economy.
A Strategic Cybersecurity Question for 2026 Leadership Teams
As organizations rethink cybersecurity after 2025, one question stands out:
If a major cyber incident occurs tomorrow, do we respond with clarity and coordination—or with improvisation?
That answer reveals the true state of resilience.
Conclusion: From Experience to Endurance
2025 provided experience—sometimes uncomfortable, often instructive.
2026 offers an opportunity to convert that experience into endurance.
Cybersecurity after 2025 is no longer about chasing threats. It is about building organizations that can withstand disruption, recover quickly, and continue operating with confidence.
The most resilient organizations in 2026 will not be those with the most tools, but those that rethought their strategy—quietly, deliberately, and ahead of the next incident. Here’s to a year of strengthened resilience, smarter strategies, and the confidence to navigate whatever challenges lie ahead.




